Lesson 5: Wallets and Self-Custody
Lesson 5: Wallets and Self-Custody
🎯 Core Concept: Self-Custody and Private Keys
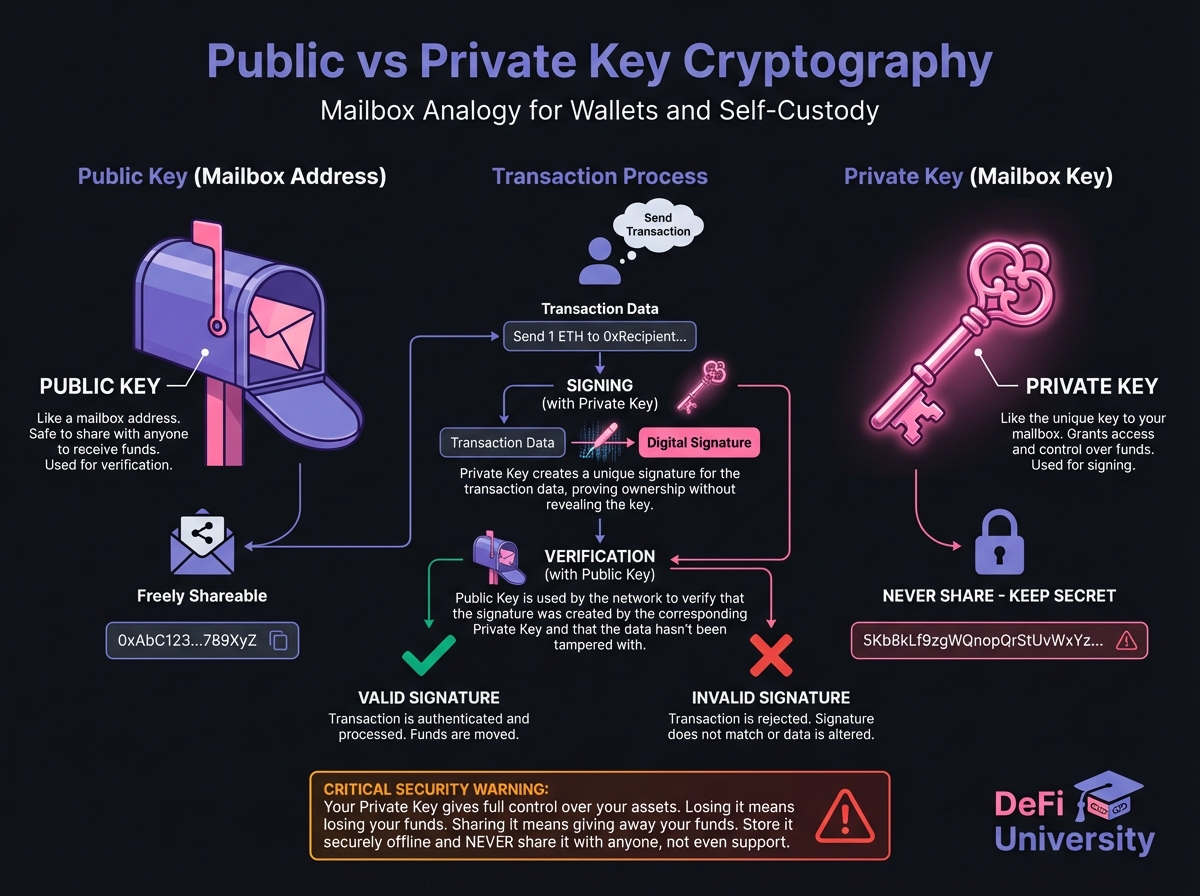
📚 Public vs. Private Key Cryptography
Public Key: Your "Mailbox" Address
Private Key: Your "Key" to the Mailbox
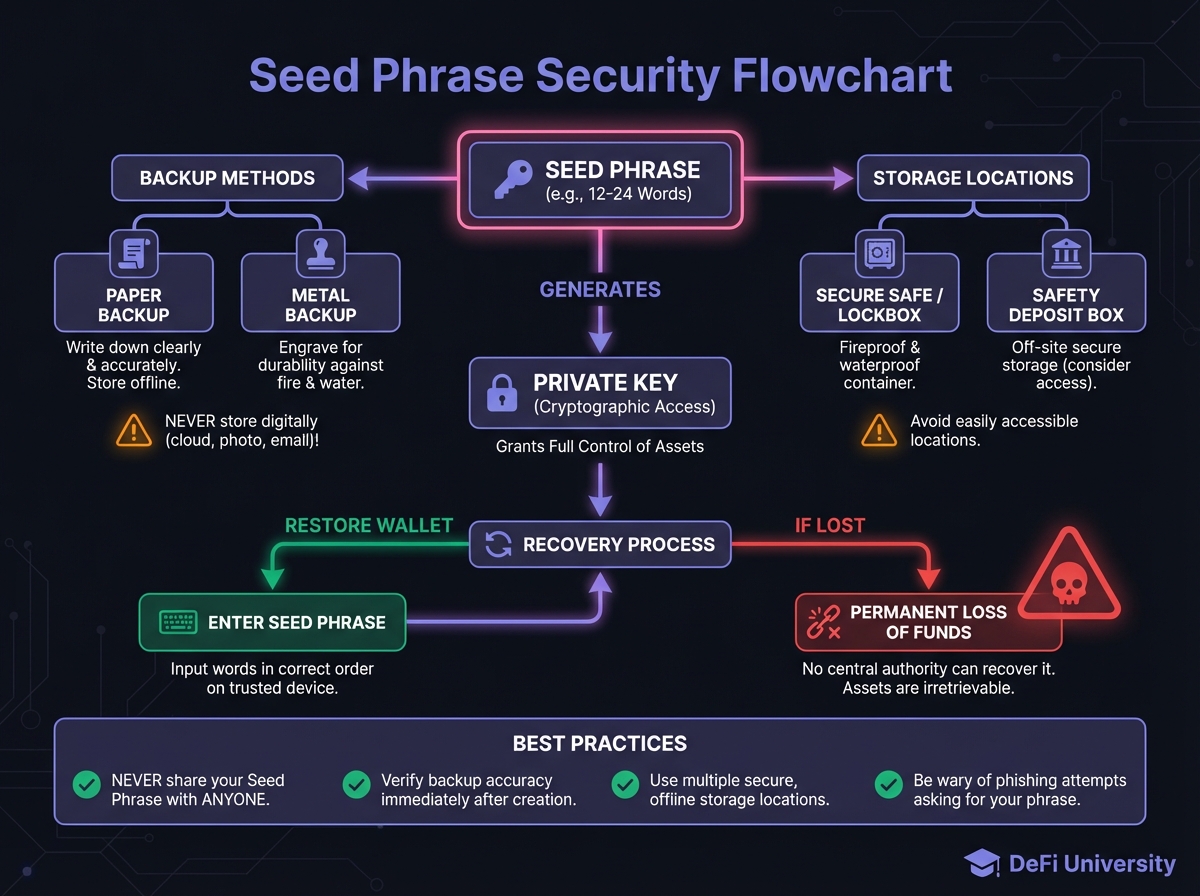
Seed Phrases: The Human-Readable Backup
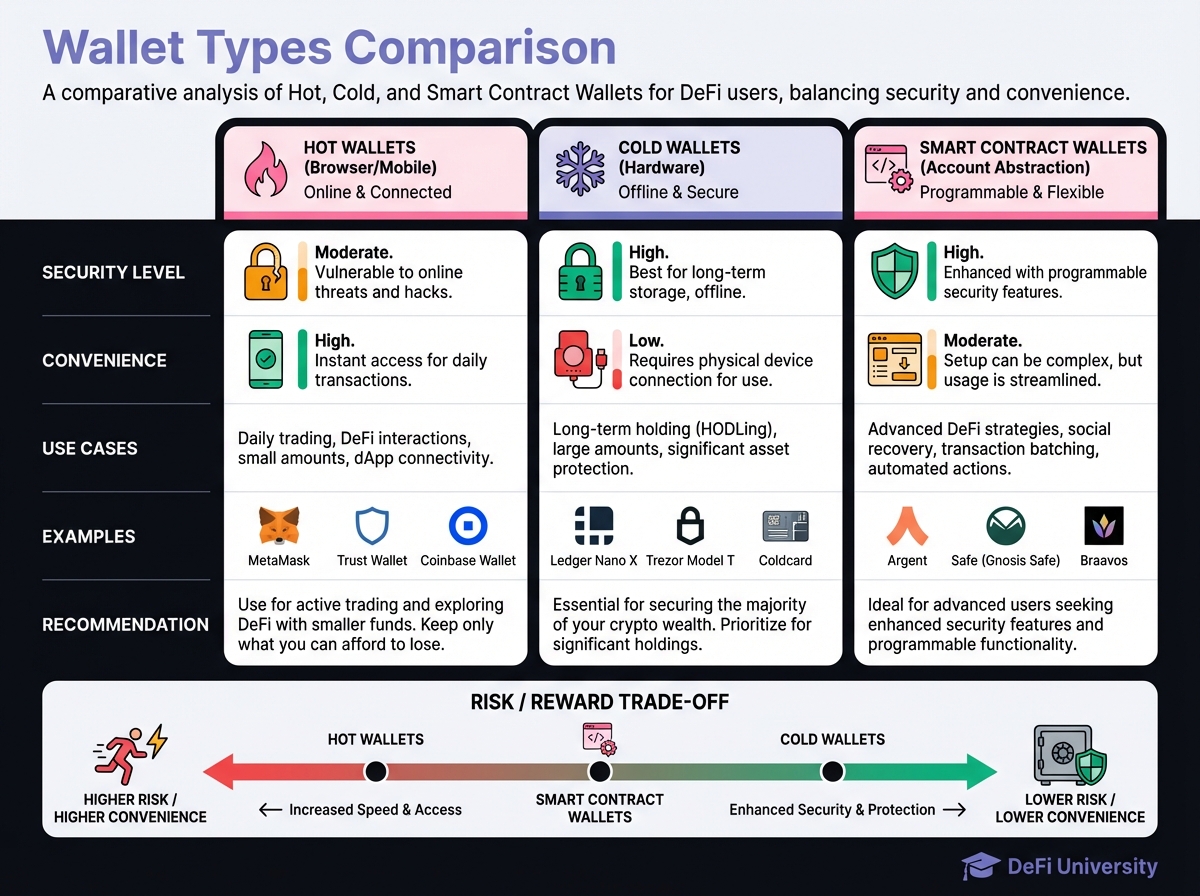
📚 Wallet Typology and Risk Hierarchies
Hot Wallets (Browser Extensions/Mobile Apps)
Cold Wallets (Hardware Wallets)
Smart Contract Wallets (Account Abstraction)
🎮 Interactive: Wallet Type Selector
🔑 Key Takeaways
📖 Beginner's Corner
Interactive Wallet Security Checklist
⚠️ Important Warnings
Last updated